Tools for the Microsoft Cloud
After hours on Twitter I have come across a lot of tools with different purpose. This note will highlight some of those I have come across that is made for the Microsoft Cloud!

I won't go into the details for each tool in this note, however I want to create separate notes for each of them where we take a closer look. Also, if you know of any other tools as well, let me know!
Stormspotter

https://github.com/Azure/Stormspotter
Stormspotter creates an “attack graph” of the resources in an Azure subscription. It enables red teams and pentesters to visualize the attack surface and pivot opportunities within a tenant, and supercharges your defenders to quickly orient and prioritize incident response work.
Ever wanted to see how everything in your Azure environment is connected? Well Stormspotter give you that ability to an extent (it is still in beta, so every node and edge type is not implemented). It gathers everything it can from given Azure credentials, parses the data and sends it to a graph database, Neo4j.
It is split into three parts:
- Stormcollector
- The data collector. You can provide credentials with the Azure CLI (az login) or using a Service Principal. The data collected depends on the permissions the provided user/sp has.
- Backend
- The backend parses the collected data and adds it to the graph database.
- Frontend
- The frontend is a webapp which visualizes the collected data stored in the database. Here you can run your own Cypher Queries to visualize the data how you see fit, or use some premade ones.
This image is from the readme showing incomming and outgoing relationships of a subscription:
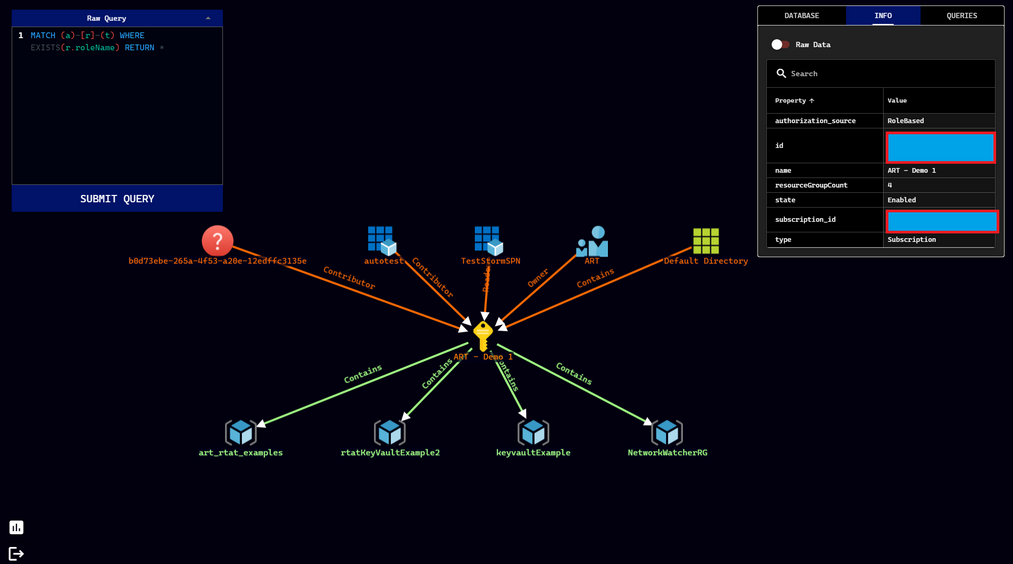
I believe this can be a great tool to find hidden relationships which implicit gives users permissions they were not supposed to have. Let me know if you can come up with some great usecases!
SkyArk

https://github.com/cyberark/SkyArk/tree/master/AzureStealth
Discover the most privileged users in the target Azure environments - including the stealthy Azure Shadow Admins.
With the AzureStealth’s scanning results - blue and red teamers can discover who are the users with the most sensitive and risky permissions. Potential attackers are hunting for those users and the defensive teams must make sure these privileged users are well secured - have strong, rotated and safety stored credentials, have MFA enabled, being monitored carefully, etc.
A great tool for taking a quick look at who has admin access so one can verify they are correctly protected or if they need to be secured better. Also highlights the problem of Shadow Admins, which don't have admin roles themselves but could escalate their role if they wanted to.
PowerZure

https://github.com/hausec/PowerZure
PowerZure is a PowerShell project created to assess and exploit resources within Microsoft’s cloud platform, Azure. PowerZure was created out of the need for a framework that can both perform reconnaissance and exploitation of Azure.
PowerZure let you quickly gather information about an Azure environment, both Azure AD and Resources. You can use PowerZure to gather security related information about your own Azure environments such as:
- All users having a certain AAD role (ex: Global Administrator).
- List all KeyVault content the signed-in user has access to.
- List all application owners.
- The owner of applications has implicit the same permissions and access as the application itself. Easily forgotten.
There is also an operational part of PowerZure. You can add AAD users and groups, add service principal secrets, download VM disks and run commands or executables on a target VM.
Table of available cmdlets from PowerZure, more info on the wiki:
| Information Gathering | Operational |
|---|---|
| Get-AzureADRole | Add-AzureADGroup |
| Get-AzureAppOwner | Add-AzureADRole |
| Get-AzureDeviceOwner | Add-AzureSPSecret |
| Get-AzureGroup | Create-AzureBackdoor |
| Get-AzureRole | Export-AzureKeyVaultContent |
| Get-AzureRunAsAccounts | Get-AzureKeyVaultContent |
| Get-AzureRolePermission | Get-AzureRunAsCertificate |
| Get-AzureSQLDB | Get-AzureRunbookContent |
| Get-AzureTargets | Get-AzureStorageContent |
| Get-AzureUser | Get-AzureVMDisk |
| Show-AzureCurrentUser | Invoke-AzureCommandRunbook |
| Show-AzureKeyVaultContent | Invoke-AzureRunCommand |
| Show-AzureStorageContent | Invoke-AzureRunMSBuild |
| Invoke-AzureRunProgram | |
| New-AzureUser | |
| Set-AzureElevatedPrivileges | |
| Set-AzureSubscription | |
| Set-AzureUserPassword | |
| Start-AzureRunbook |