Writeup: PHST 2021
Another great CTF event hosted by https://pst.no, this time with an Easter theme 🐣! I got some more experience with OSINT, reading and understanding source code, and scripting.

Skjærtorsdag

The first day we get introduced to the gang. Anetti Bac is posting a picture on Instagram and Mikael Foks asked to be tagged with his user @mikaelfoks1337.
One can find an Instagram user by navigating to instagram.com/{USER}. This makes it easy to find Mikael Foks's user, and our next hint: "Du finner meg der fuglene kvitrer 🦊" which roughly translates to "You can find me where the birds tweet 🦊".
My first guess is to find his user on Twitter. However there is no user with the name @mikaelfoks1337. Twitter let us search for users tho, and searching for "Mikael Foks" provides us with his user; @FoksMikael.
On his profile he links to https://robotanekjem.p26e.dev, with the only content on the site being: 🔜🤖🤖🤖. Based on the subdomain name, which translates to the robots are coming and the robot emojis, checking out robots.txt gives us the new hint:
# Usj, roboter, ha dere vekk!
User-agent: \*
Disallow: /94afc738_det-første-flagget.html
and navigating to that html-file, gives us the first flag: PST{snart_er_det_SOMEr}
Langfredag

On the second day the Eggchange Server seems to have crashed. It appears that a consulting firm have just ran a update, and we are handed the eventlog of the server. Also notice the note on the monitor with what might be a password 43mm3l1g437.
Here is a sample of the eventlog.txt:
...
[EGGSCHANGE] Update-EggContent id=e7337af9d58444dabfe2728963723ce1
[EGGSCHANGE] Update-EggContent id=3da366c52aff4c6d8c15e38dca579bd9
[EGGSCHANGE] Update-EggContent id=805b73fa0b9f4e13a37280e6b1725738
[EGGNET] Get-EggsChangeHealth
[EGGSCHANGE] Update-EggContent id=335e5b9aba3b4434be7d4c340607c478
[EGGSCHANGE] Send-HealthStatus status=ok
[EGGSCHANGE] Get-EggStatus id=8d4d00ca5b3a496fa2acbc976caeaa63
[EGGSCHANGE] Get-EggStatus id=39ee50597789482c93675b031a0f05d3
[EGGSCHANGE] Get-EggStatus id=e10de5b0fe2147b98fa3ca314a06f752
[EGGSCHANGE] Update-EggContent id=5e849d8a372e41dcb711baeac8b559a3
[EGGNET] Set-EggsChangeHealth health=ok
[EGGSCHANGE] Update-EggContent id=7efcf782a2ef44c289bb6c03a604e511
[EGGSCHANGE] Get-EggStatus id=3c75f7cc65644e1e85ed267a130b90fa
[EGGSCHANGE] Get-EggStatus id=b92e371cbd854c469933ff3fe7a631bb
...
It seems to be some form of Powershell parody, so the next I did was to see what commands the eventlog contained:
cat eventlog.txt | awk '{print $2;}' | sort | uniq -c | sort
1 Get-AvailableEggnetUpdates
1 Get-NewUpdate
1 Install-NewUpdate
1 Recieve-NewEggsChangeUpdateUrl
1 Send-NewEggsChangeUpdate
1 Set-AlarmStatus
1 Set-EggsChangeHealthTimeout
1 Set-NewEggsChangeUpdateUrl
1 Set-UpdateStatus
113 Send-HealthStatus
113 Set-EggsChangeHealth
114 Get-EggsChangeHealth
301 Get-EggStatus
330 Set-DeliveryAddress
357 Update-EggContent
Now the first one that got my attention was the Set-NewEggsChangeUpdateUrl so I found it in the eventlog and found a git user and repository, https://github.com/paaschecomsulting/eggschange.
After going through the repository there was some stuff to take note of. The first was the newest commit, where someone changed the UbuntuKeyserverUploaded and added DeveloperFingerprintPrefix. Ducking UbuntuKeyServer lead me to https://keyserver.ubuntu.com/. Here we can search for the fingerprint with the prefix and find:
pub rsa4096/616341b190ef25ce024dd2e9494450ef40d37e5c 2021-03-26T11:49:10Z
Hash=0687169093e51a410dc6168fbdacbc4f
uid Haha, tror dere jeg er så dum at jeg skriver navnet mitt her?! (Dere fanger meg aldri!) <ff0000sild@protonmail.ch>
sig sig 494450ef40d37e5c 2021-03-26T11:49:10Z ____________________ ____________________ [selfsig]
sub rsa4096/18575873bda0dc699a321b4ade946099bbeca0f8 2021-03-26T11:49:10Z
sig sbind 494450ef40d37e5c 2021-03-26T11:49:10Z ____________________ ____________________ []
An e-mail, and a message. No flag.
The second thing I took notice of was the two strange files Helper1 & Helper2 and the function Test-EggschangeFlag:
function Test-EggschangeFlag () {
param(
[parameter(Mandatory=$true)]
$Decryption_key
)
Function ConvertTo-UnsecureString {
Param (
[Parameter(Mandatory=$True)]
[System.Security.SecureString]$ss
)
Try {
$ptr = [System.Runtime.InteropServices.Marshal]::SecureStringToGlobalAllocUnicode($ss)
[System.Runtime.InteropServices.Marshal]::PtrToStringUni($ptr)
}
Finally {
[System.Runtime.InteropServices.Marshal]::ZeroFreeGlobalAllocUnicode($ptr)
}
}
$Kryptert_påske = "76492d1116743f0423413b16050a5345MgB8AHoAdQA2ACsAUABWADkAbQBvAGMAYgBDAGgASQB6AGUAdgBxAGgASQBQAGcAPQA9AHwANwAxADkAMAA2ADIANwAwADIAZgAzAGMAZgA5ADkAMgA1AGQAZQA3ADYAOQBjADAAYQAzAGQAMgA2AGEAMAAxADcAYQBjAGIANABmAGQANwA0AGUAYQBhADAAMABlADIAMABjADQANwBiAGMAZAA4ADUAOQAwAGQANABiADQAMQA0AGMAMwA0ADAAMABiADcANwA5ADkAZQA4ADkAMgA5AGYAYwAwADcAMAA5ADIAMwBmADQANgB
kAGEAMwBlADgANAAxADYAOAA0ADMAMQA4ADYANQBlADIAZgA1ADcAOAA3AGMAYwA0ADIANgBhADMAYQBkADMAOAAxAGQAMAA2ADQAYwA3ADAAYQBmAGMAMgBkAGUAZQBmADQAMQBmADcAMAAzAGEAYwBhADMAYwBjAGMAOQBlADcANABiADIAMAA="
try {
$Decryption_key = $Decryption_key.tolower()
$key = [byte[]]($Decryption_key).ToCharArray()
$ss = ConvertTo-SecureString -String $Kryptert_påske -Key $key
$Flag_decoded = ConvertTo-UnsecureString $ss
return ([regex]::Matches($Flag_decoded,'.','RightToLeft') | ForEach {$_.value}) -join ''
}
catch {
Write-Host "Feil nøkkel nøklet i nøkkelhullet. Prøv igjen." -ForegroundColor Red
Write-Host "Spør om hjelp kanskje?"
}
}
Now back to the two strange files. After downloading them I ran file on each to see what kinda files they were. Both turned out to be images, so the next low hanging thing I ran since it is a CTF was strings and notice something peculiar in the start of both file:
[hLa%(I.
^^^^^^^^^^^^/==============\|* JPG image *|| with || identical || -prefix || MD5 collision|| || by
|| Marc Stevens || and ||Ange Albertini|| in 2018 ||* *|\==============/vvvvvvvvvvvvvvvv
JFIF
"Exif
$3br
...
No this can't be a coincidence. Now, the function need a decryption key and if you fail to provide the new one you are told to "Ask for help maybe?". Providing the MD5 sum of the two strange files as the decryption key gives us the flag: PST{PaascheStemning_og_Kraftskall}
Påskeaften

This day we are investigating a weakness in a custom network protocol called EGGNET. We are also provided with a pcap-file. Both in the comic and the traffic we are pointed to a open source repository on Github: https://github.com/paskeharen/eggnett-client.
Now, this is coded in Rust, and I'm not a developer, but after a few minutes I had a good feel on what the code did. From what I understood; it takes in a password, and listens to key input, then combines the password and input and sends the MD5 sum of the concatenated string in the header X-EGG.
First I tried the default password that we can see in the code; ***********. I concatenated the most used characters (a, e) at the end like the protocol does, and checked the MD5 sum with any of the X-EGG values in the pcap-file.
cat nettverkstrafikk.pcap | grep -a 'x-egg' | awk '{print $2;}'
There was no match so it was more possible it might be another password. Now looking back to yesterday, we got a password from the monitor. Using the same steps as above I found the MD5 sum for both a and e! Now next step was to script every other char...
import hashlib
payload = ""
pw = "43mm3l1g437"
lookupMD5 = {}
for asciiC in range(32,254):
md5string = pw + chr(asciiC)
lookupMD5[hashlib.md5(md5string.encode('utf-8')).hexdigest()] = chr(asciiC)
xegg_file = open('MESSAGE_encoded.txt', 'r')
count = 0
while True:
count += 1
line = xegg_file.readline()
if not line:
break
try:
payload += lookupMD5[line.strip()]
except:
print()
print("bom: " + line.strip())
xegg_file.close()
print("payload:\n" + payload)
payload:
BEGYNN\r\nEGGNETT KONFIGURASJON SETT oppdateringskilde TIL https://github.com/paaschecomsulting/eggschange\r\nEGGNETT KONFIGURASJON SETT OBFUSKERT flagg TIL "When the stars line up And you catch a break People think you're lucky"\r\n
Now this didn't give us any flags, but what looks to be a hint. Ducking the quote leads you to a song called "Timing is everything". This made me take a look at the timestamps of the traffic:
cat nettverkstrafikk.pcap | grep -a 'Date' | uniq -c
54 Date: Fri, 02 Apr 2021 12:37:10 GMT
87 Date: Fri, 02 Apr 2021 12:37:11 GMT
20 Date: Fri, 02 Apr 2021 12:37:12 GMT
1 Date: Fri, 02 Apr 2021 12:37:13 GMT
3 Date: Fri, 02 Apr 2021 12:37:14 GMT
2 Date: Fri, 02 Apr 2021 12:37:15 GMT
2 Date: Fri, 02 Apr 2021 12:37:16 GMT
2 Date: Fri, 02 Apr 2021 12:37:17 GMT
5 Date: Fri, 02 Apr 2021 12:37:18 GMT
2 Date: Fri, 02 Apr 2021 12:37:19 GMT
3 Date: Fri, 02 Apr 2021 12:37:20 GMT
2 Date: Fri, 02 Apr 2021 12:37:21 GMT
1 Date: Fri, 02 Apr 2021 12:37:22 GMT
3 Date: Fri, 02 Apr 2021 12:37:23 GMT
2 Date: Fri, 02 Apr 2021 12:37:24 GMT
2 Date: Fri, 02 Apr 2021 12:37:25 GMT
3 Date: Fri, 02 Apr 2021 12:37:26 GMT
5 Date: Fri, 02 Apr 2021 12:37:27 GMT
2 Date: Fri, 02 Apr 2021 12:37:28 GMT
2 Date: Fri, 02 Apr 2021 12:37:29 GMT
2 Date: Fri, 02 Apr 2021 12:37:30 GMT
2 Date: Fri, 02 Apr 2021 12:37:31 GMT
4 Date: Fri, 02 Apr 2021 12:37:32 GMT
3 Date: Fri, 02 Apr 2021 12:37:33 GMT
2 Date: Fri, 02 Apr 2021 12:37:34 GMT
2 Date: Fri, 02 Apr 2021 12:37:35 GMT
4 Date: Fri, 02 Apr 2021 12:37:36 GMT
2 Date: Fri, 02 Apr 2021 12:37:37 GMT
1 Date: Fri, 02 Apr 2021 12:37:38 GMT
2 Date: Fri, 02 Apr 2021 12:37:39 GMT
6 Date: Fri, 02 Apr 2021 12:37:40 GMT
Now almost all traffic was sent in 2 seconds, then we see a major change in the packages per second. This correlates with a TCP stream that start arount 12:37:12. Now I had a real tough time solving this one, and after getting a hint, it was right in front of me. Using Wireshark's tool TCP Stream Graph and looking at the time sequence, we see a clear pattern:
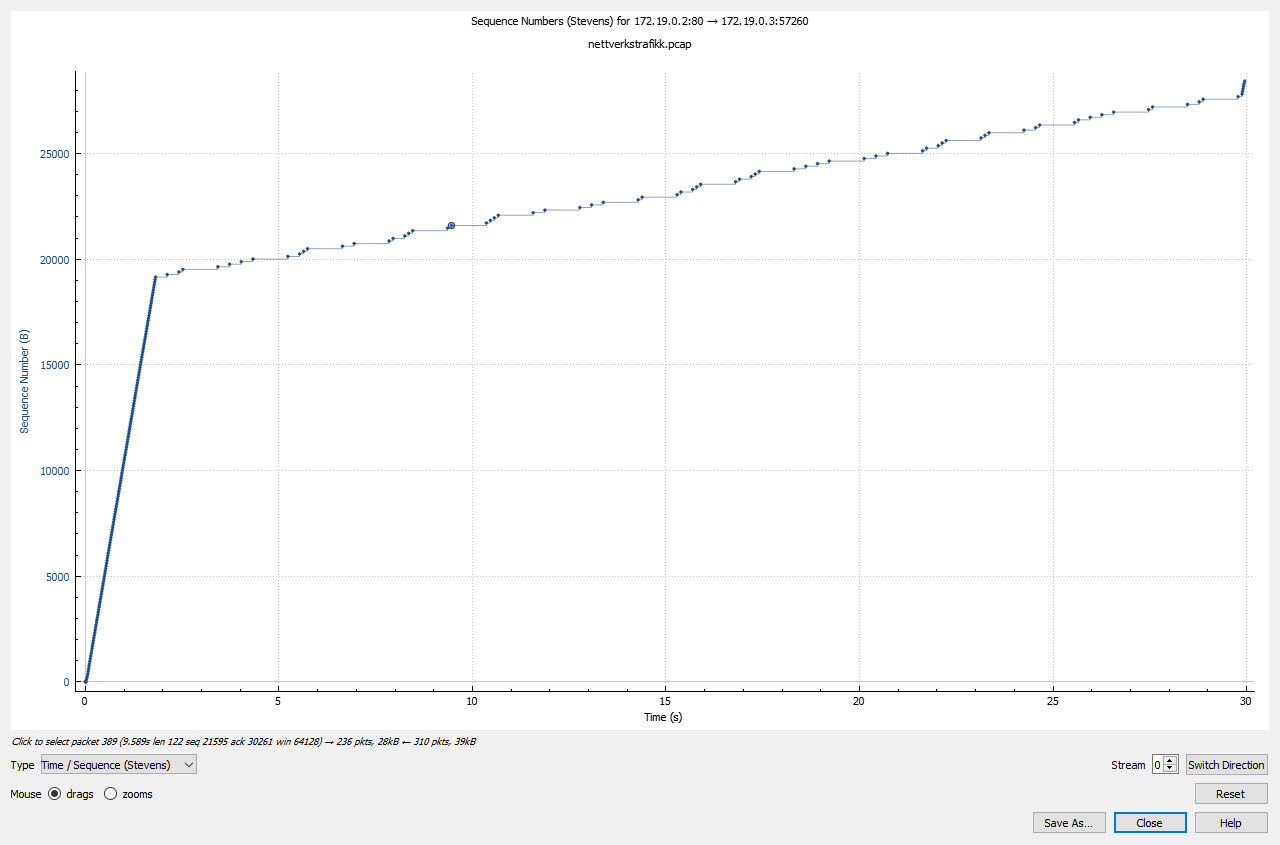
And in the comic there is a reference to Morse Code. Having this in mind:
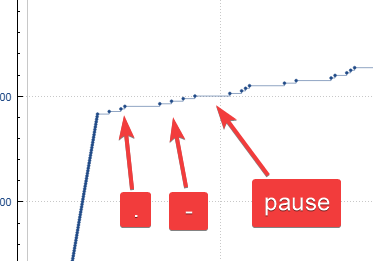
We get --. --- -.. - .-.. . ... - -- . .-.. .-.. --- -- .-.. .. -. .--- . -. ., or GODTLESTMELLOMLINJENE, which between the prefix and suffix was the flag!
1 Påskedag

We are now looking for the adversary. The only hint we get from the comic is a user on Tumblr, tastatur-og. Going to that profile we see one post and a message saying to "send me an e-mail". Clicking the picture also takes us to the Flickr source where the we can see the EXIF description say: Send me a message if you want todays flag. Now the only e-mail we know of is the one we found on Langfredag, ff0000sild@protonmail.ch. Sending a mail to this address gives us the flag: PST{tr4ckp4d_3r_n0e_he2k!}.
Wrapup
PHST2021 lives up to the standards I experienced during the NPST2020, PST's Christmas CTF. Another great event. Hope you enjoyed this writeup!
Itj fårrå nålles, HB