What and why
Canarytokens is a free, easy-to-implement and set-n-forget tool to get alerted when someone triggers them. Let's look at how they work and how to make our own custom with Azure Logic Apps.
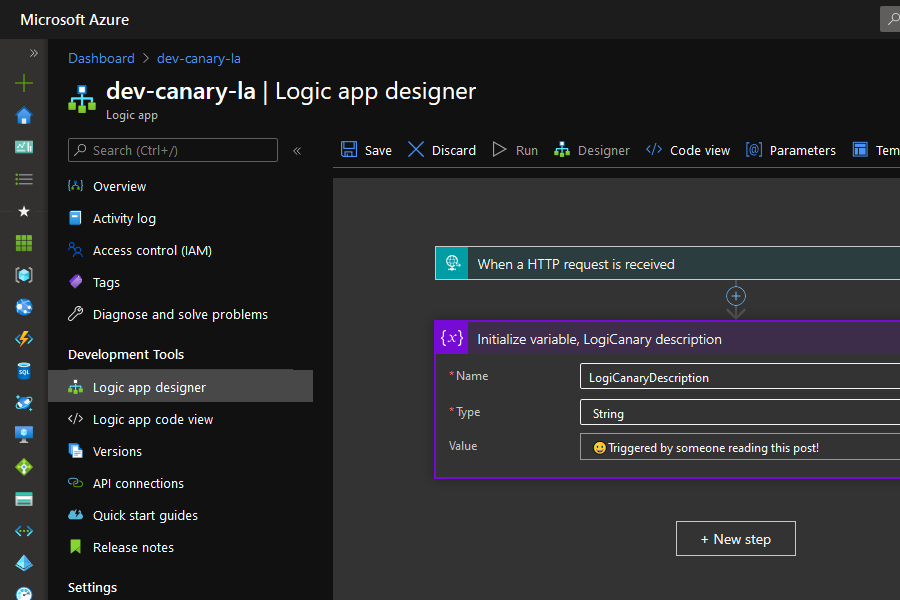
Canarytokens basically works as an alert on a GET request. They let you add your mail or a webhook as alerting method and when the trap is sprung, you are alerted with the message you configured when initially creating the token. This could be a simple message as "Someone opened the password.docx on ImportantServer-01's desktop" which might imply that someone is snooping around or a poor admin forgot a password... Anyway something one should look into!
The limitations of alert methods (mail and webhook) and the reputation of Canarytokens (positively, adversaries could block requests to canarytokens.com) lead me to look into recreating the functionality with Azure Logic Apps. As a response to the limitation they also provide the source code and Docker images so you can run it yourself. When it comes to the URL of Logic Apps it's tougher to block them, since some might actually be used to something other than traps, making the decision to block the domain harder.
LogiCanary (trademark not pending at all) lets us add more functionality to the alert.
This is just some examples of what to do. Be creative and let me know how you do this!
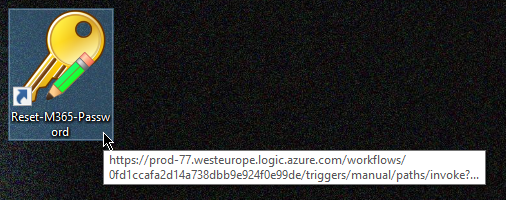
Desktop Shortcut
Create a shortcut on a high value targets (CEO, CFO, etc.) desktop and give it a juice name and icon. You also need to instruct the users, whom you would expect to find the tokens, to not click on them.
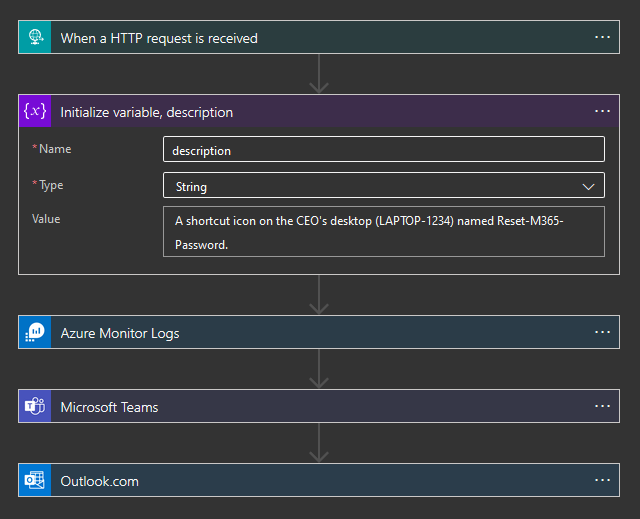
Now with this info we can:
- Get sign in logs for the user from Log Analytics
- Post a message in the "SOC" channel in Teams containing:
- The description of the token
- The last 10 sign in logs for the CEO
- Information that a decision email has been sent to the security admin to disable the user account or not.
- Email the security admin with the option to disable the user to prevent further abuse.
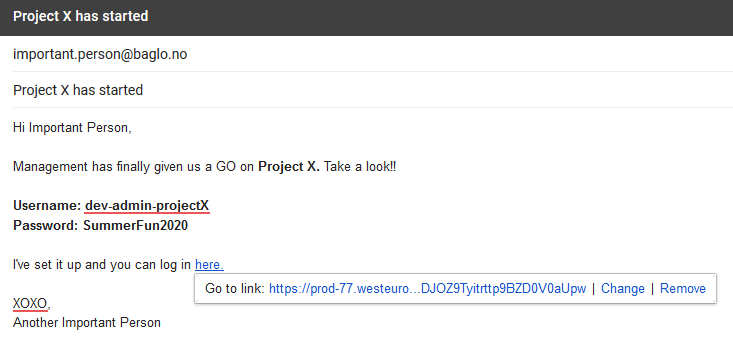
Internal "Important" Email
Insert the LogiCanary in what seems to be an important mail. Leave it in the mailbox, archive it or download the mail and back it up somewhere.
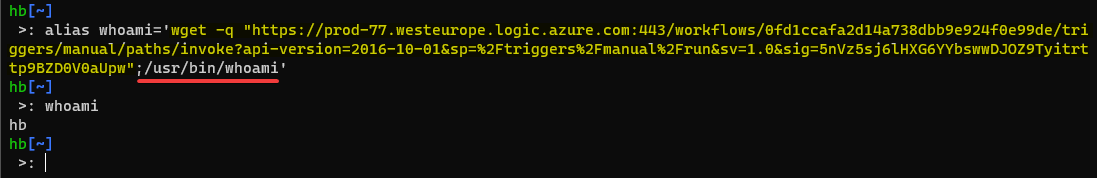
Sneaky Command
By aliasing a well known command on a server you can silently set off the LogiCanary:
Links in documents
This could be Word, Excel or PDF.
Alerting on user login
Add the LogiCanary to a user's .bashrc or Powershell PROFILE.
How
Create a new Logic App however you like. I'd recommend having an own resource group for all your LogiCanary. Naming them so you can know what triggers them and where they are placed is also recommended.
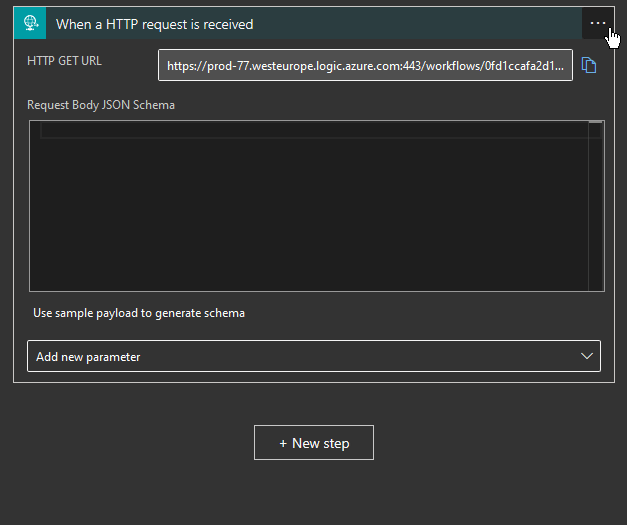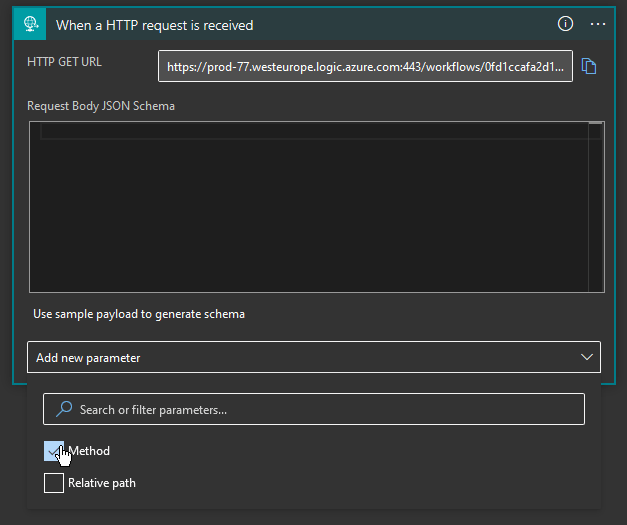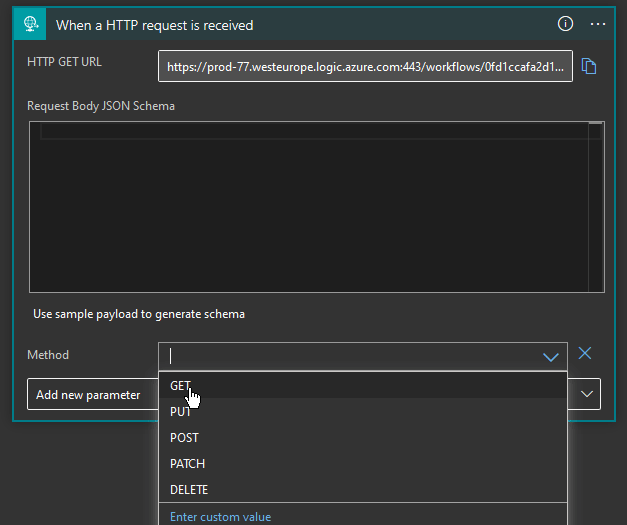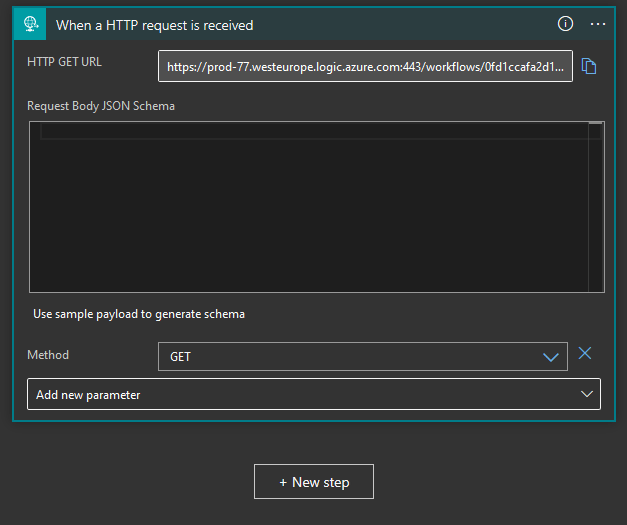
When setting up the trigger pick When a HTTP request is received and go into the design view.
Here you need to add that we want to change the Method and pick GET.
Now the Logic App is ready for your creativity. Add steps as you please to create a powerful, cheap, easy-to-implement and set-n-forget alert solution. When it comes to placement of these you can draw inspiration from https://docs.canarytokens.org/guide/, altho I haven't gottn everyone to work as I wanted due to the nature of Logic App request URL. Let me know if you catch something 🤠
If I get the time I might create some Logic App ARM templates for a few LogiCanary. We'll see!
Itj fårrå nålles,
HB