Detecting MITM attacks with Microsoft Sentinel
Lately there has been an increased focus on Man-In-The-Middle (MITM) attacks, highlighting the limitations of traditional Multi-Factor Authentication (MFA) as a comprehensive solution for account security. Easy-to-use tools, like Evilginx, have made it simpler for adversaries with different skills to carry out phishing attacks with little effort. This has led to the adoption of phishing-resistant MFA methods, such as FIDO2 security keys or Windows Hello for Business.
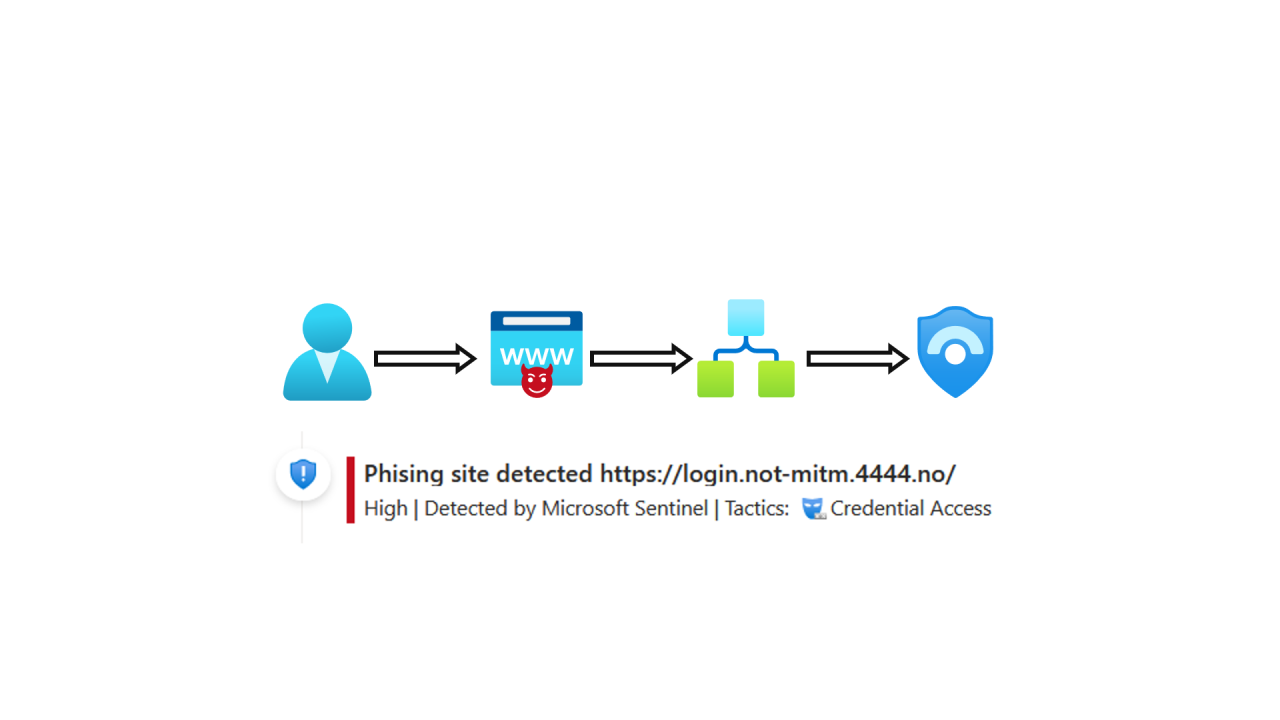
As we wait for more widespread use of phishing-resistant MFA, it is important to detect potential phishing sites trying to trick users. The idea from Wesley Neelen @ Zolder BV, involves using custom CSS in your tenants' Company Branding. This CSS sends a request to a specific endpoint, which validates if the referrer is the legitimate login.microsoftonline.com or another suspicious site.
My contribution will focus on how to connect this approach to your security monitoring using Azure tools such as Logic Apps and Microsoft Sentinel. This integration enhances your ability to spot and respond to potential threats effectively.
You can read Wesley Neelen blog here.
Prerequisites
Add company branding to your organization's sign-in page - Microsoft Entra | Microsoft Learn
Adding custom branding requires one of the following licenses:
- Microsoft Entra ID P1 or P2
- Office 365 (for Office apps)
The Global Administrator role is required to customize company branding.
How it works
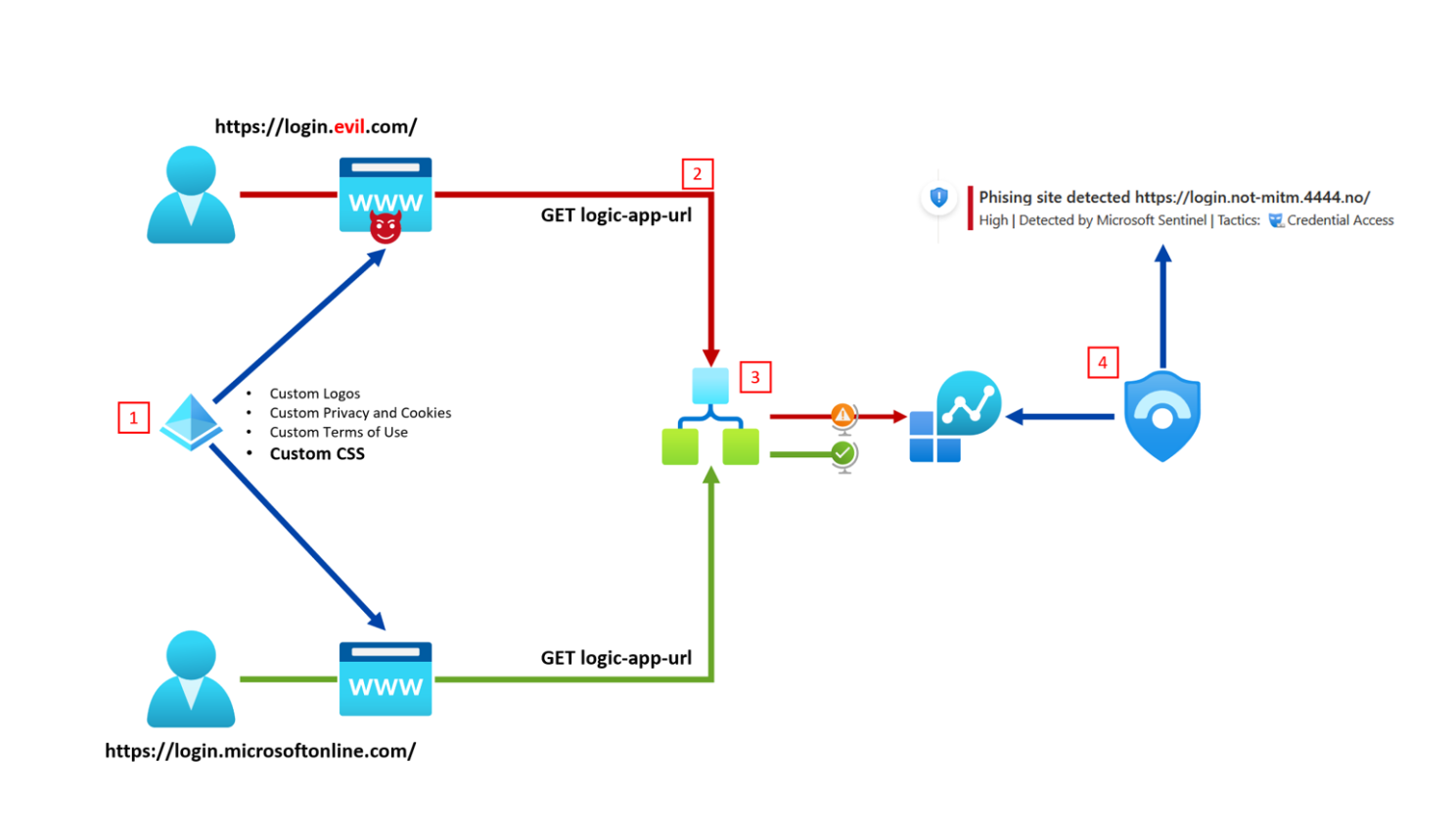
- Microsoft tenants offer the flexibility to customize your user's login experience by uploading custom media, like logos or, in our case, a custom CSS file. This CSS is loaded each time a user accesses the Microsoft login page directly or through a Man-In-The-Middle (MITM) proxy.
- When the user's browser loads the CSS, it sends a request for an image to your Logic App containing the crucial REFERER header.
- Your Logic App receives the image request, even though the image does not exist. It checks the REFERER header to confirm whether it's from Microsoft or an imposter. If it is someone pretending to be Microsoft, the information is logged into Log Analytics for Microsoft Sentinel.
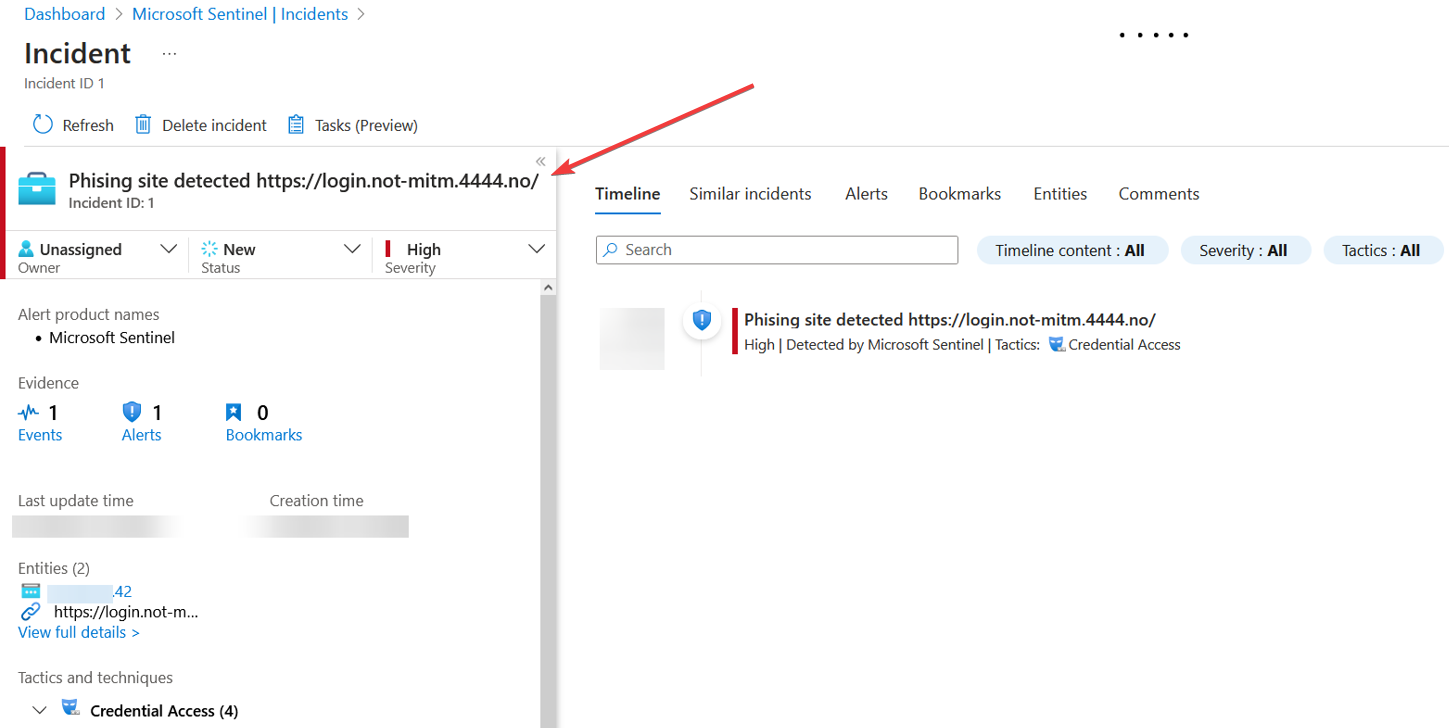
- Microsoft Sentinel is configured with an Analytic Rule for any logs originating from the Logic App. It triggers the creation of an Incident, prompting your team to take appropriate action.
The "Referer" Header
The Logic App spots potential phishing sites by checking the Referer header, which every modern browser sends when requesting content, that discloses the initiating URL of the request.
- ✅ Referer: https://login.microsoftonline.com/
- ❌ Referer: https://login.not-mitm.4444.no/
You can read more about the header here: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Referer.
The Logic App
To get started, deploy the Logic App, here I just use a Consumption Plan, since it is the easiest to start with and deploy.
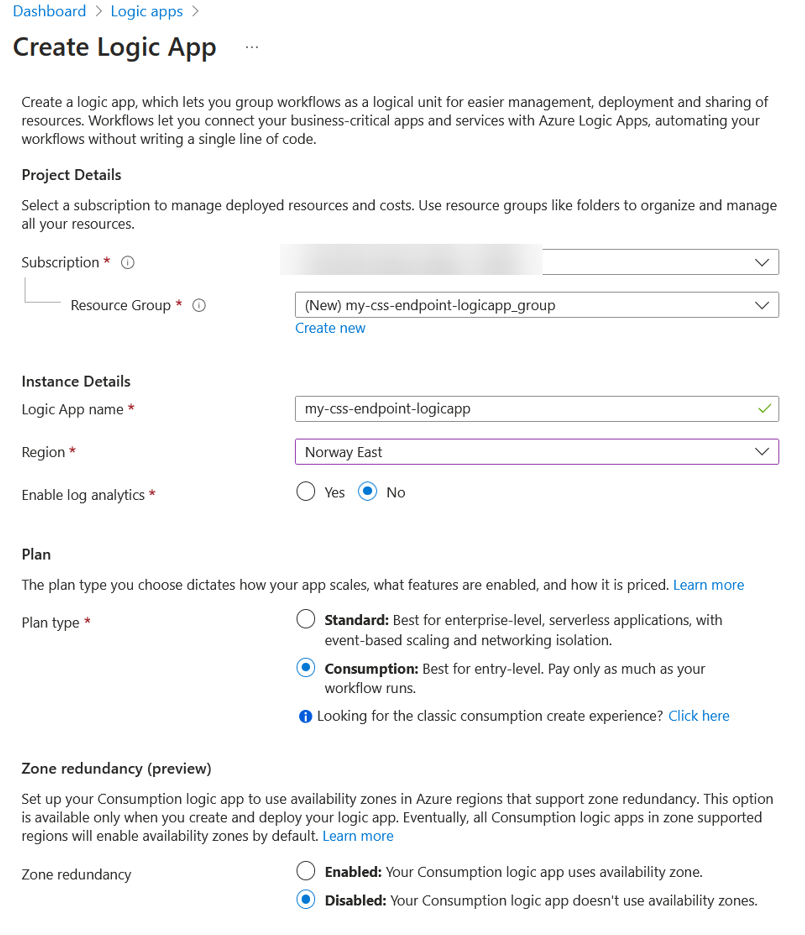
Once you have it up and running, navigate to the Logic App Designer and pick the trigger "When an HTTP request is received".
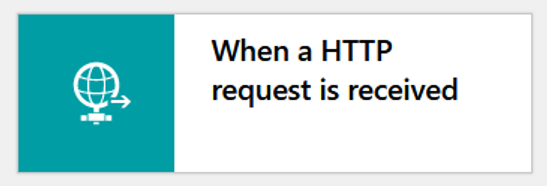
Leave the Request Body JSON Schema empty, add the parameter Method, set it to GET, then save the Logic App. This will give you the URL you need for the Custom CSS part, you will need this later.
Configure the rest of the Logic App as seen in the image below. Or get more details here: https://github.com/baglo/azure-lures/tree/main/mitm-detection-logicapp.
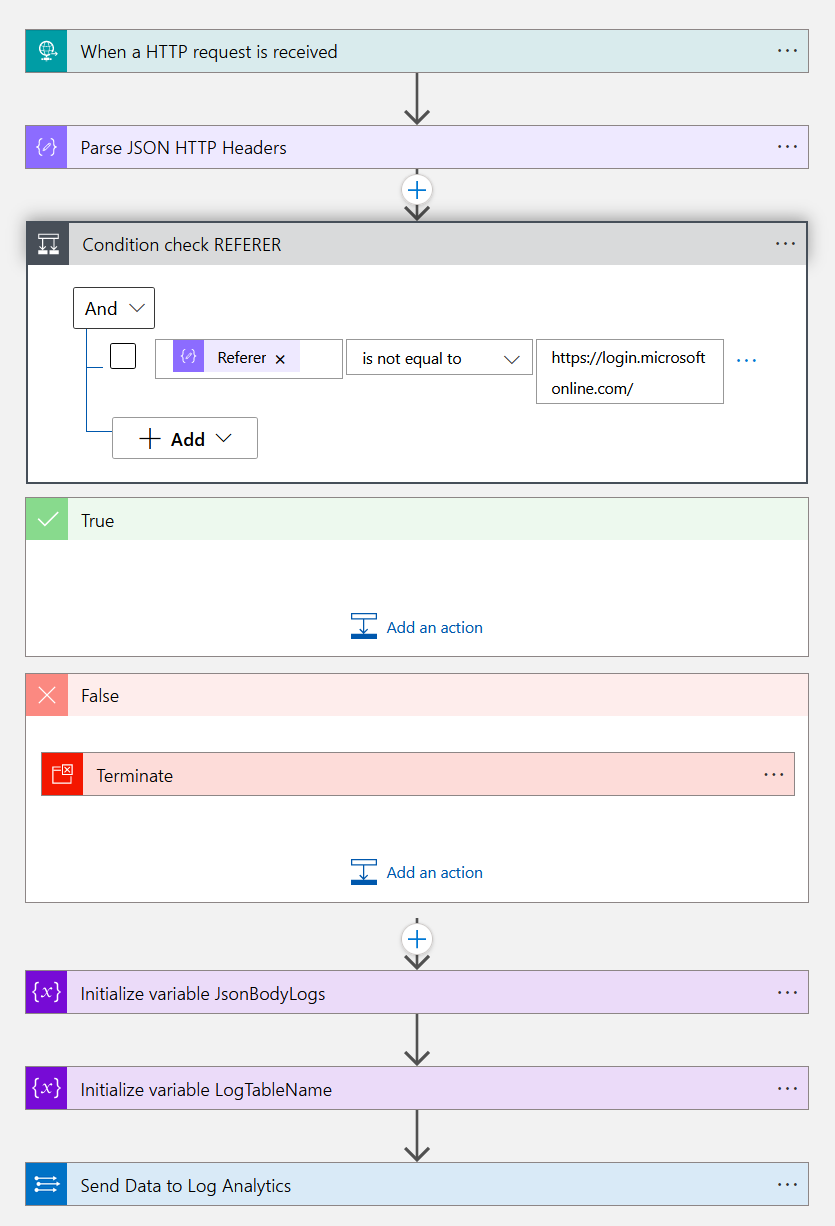
Configuring Microsoft Sentinel
Create a new rule to detect logs coming in from the Logic App. I recommend using a Near-Real-Time (NRT) rule to be notified as fast as possible if a phishing site is detected. If you have maxed out your NRT rules, it is possible to use a regular Scheduled Rule that runs every 5 minutes.
Configure the rule with the following (if not mentioned, default is implied):
- Name: Potential Phishing site detected
- Description: A user might have accessed a phishing site pretending to be a Microsoft login page. Investigate this user by looking at sign-in logs and looking at the IP entity provided in this alert. When the targeted user has been identified, the recommended actions are revoking all sessions, and requiring the user to set a new password.
- Severity: High
- Tactics and techniques: Credential Access (T1557, T1539)
- Rule Query (Pay attention to the table used here if you changed the name in the Logic App):
AzureLure_CL
| where LureType_s == "MITM Detection Custom CSS"
| extend Entity_ClientIP = ClientIp_s
| extend Entity_URL = Referer_s
- Entity Mapping: IP Address -> Entity_ClientIP, URL -> Entity_URL
- Alert Details > Alert Name Format: Phising site detected at
{{Entity_URL}}
Now Microsoft Sentinel is ready to monitor for phishing sites.
The Custom CSS
Note that if your organisation already uses Custom CSS, you might have to make changes to the existing file and re-upload it.
Create a local file named custom.css and add the following:
.ext-footer {
background-size: 0 0;
background-image: url('URL-COPIED-FROM-LOGICAPP');
}
¨ Navigate to the Microsoft Entra Admin Center, go to User Experience, Company Branding, and click edit:
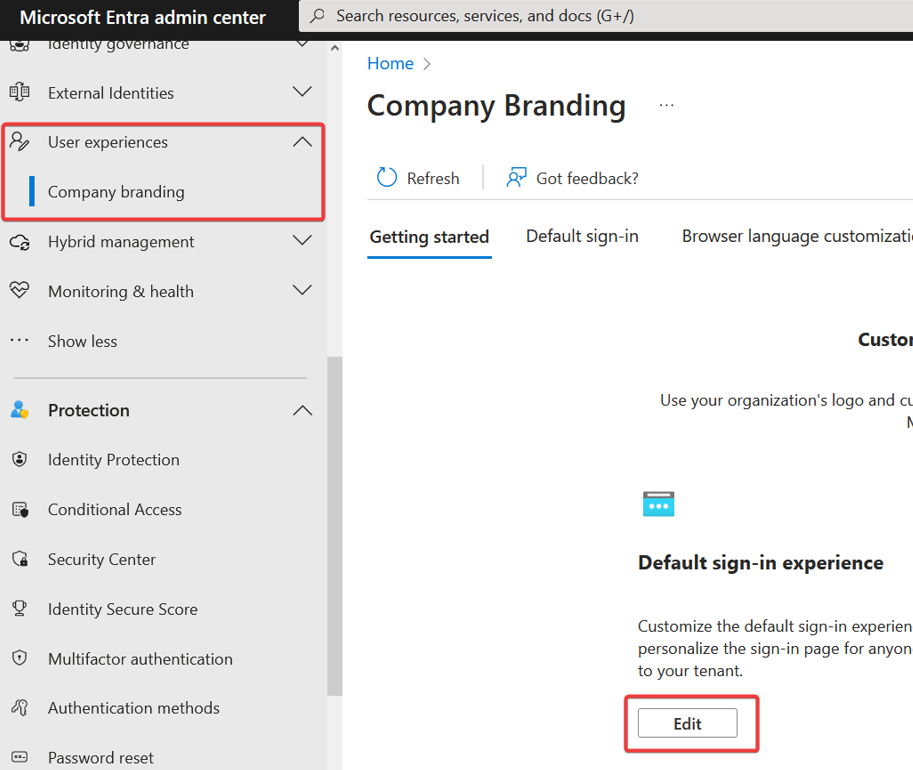
Go to the Layout tab and scroll to the bottom, here you can upload your custom CSS file. Once complete, review and save. After this, all users trying to log in will get the CSS, triggering your Logic App.
Validating functionality
Legit sign-in
In a private browser window, navigate to https://office.com, click sign-in, enter your email, and click next. At this point, the custom CSS will run!
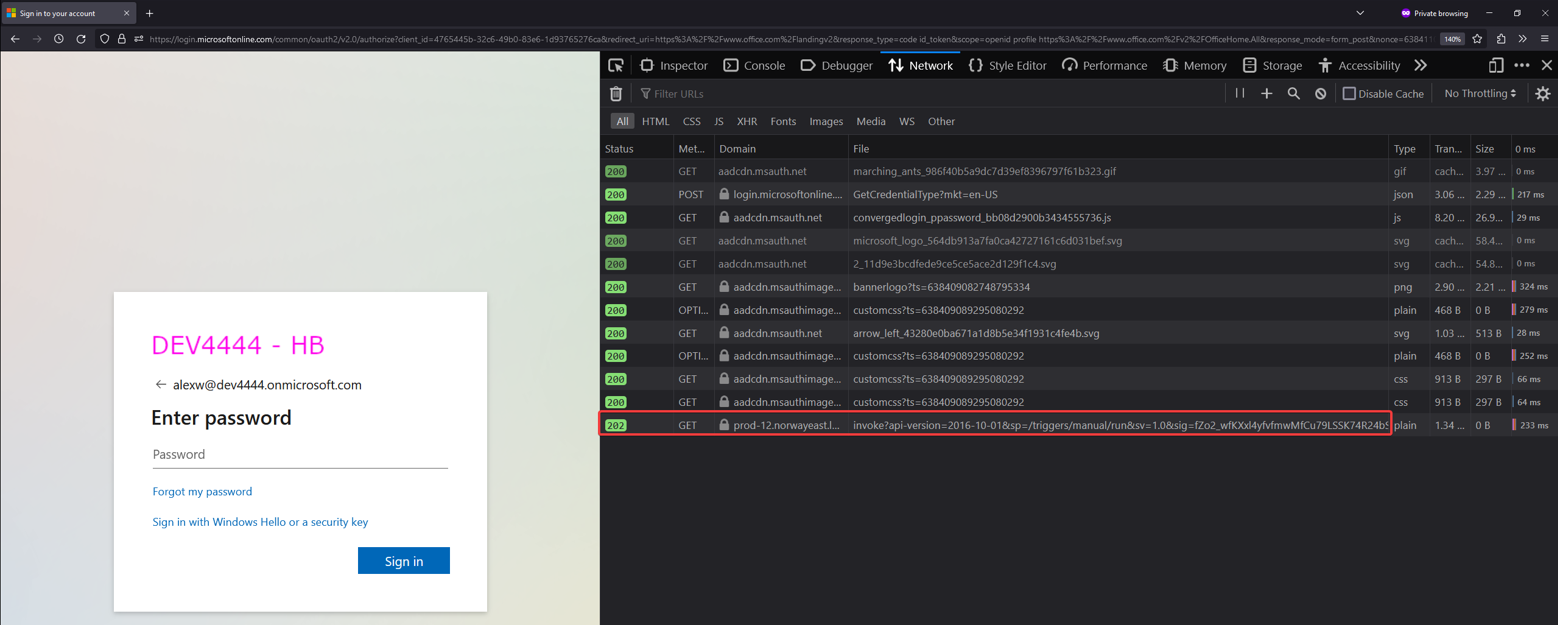
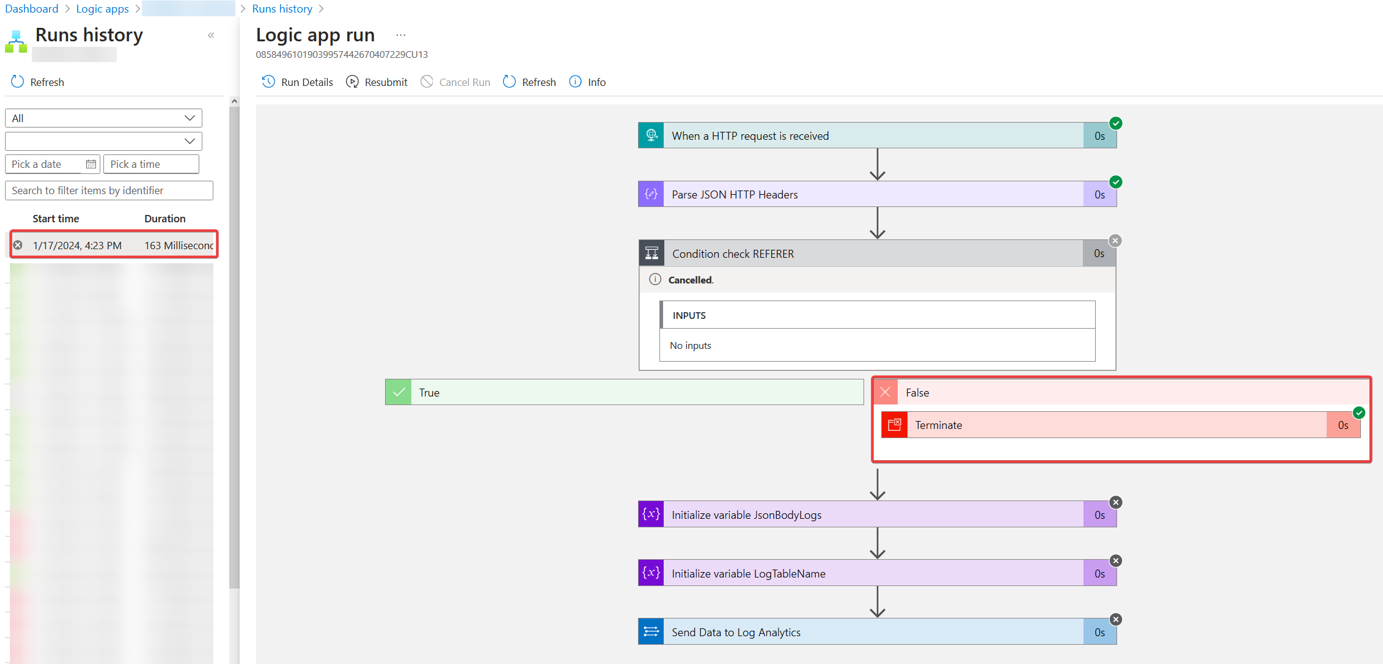
We can also look at the run-history of the Logic App and see that it was terminated as expected, since this was a legit sign-in from https://login.microsoftonline.com.
Testing with Evilginx
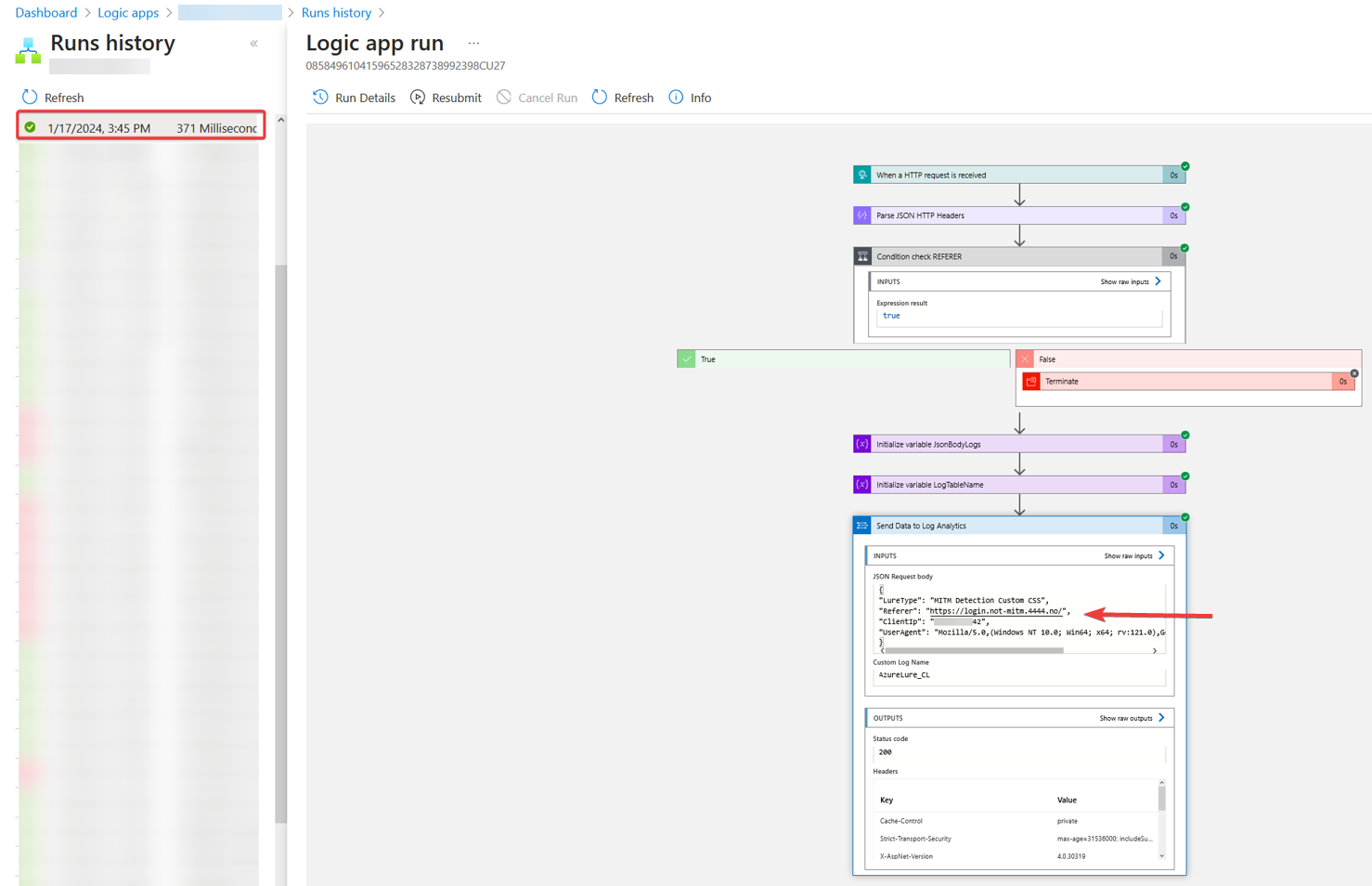
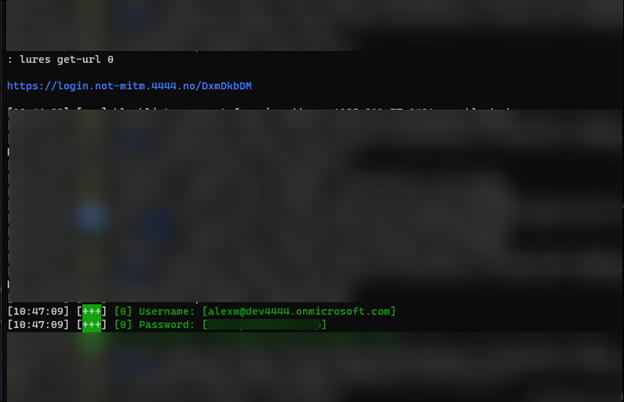
I will not go into detail on how to set up and configure Evilginx, but it will let you validate that your flow to Microsoft Sentinel works. After clicking your phishing link, entering your email, and clicking next:
Some security automation ideas
Incident Management
- Send an alert with incident information to an email address.
- Send an alert with incident information to a Microsoft Teams channel.
Enrichment + Investigation
- Add a Whois lookup to gain more insight about the phishing domain and add the info as a comment on the incident.
- Get information on the IP associated with the phishing domain and add this as a comment on the incident.
- Get all recently signed-in users that came from the same IP as the phished user, and add them as a comment on the incident.
Remediation
- Add a deny rule in your organisation's firewall to stop other users from accessing the phishing URL.
Summary and some thoughts
Throughout this article, we looked at a simple way to improve your organisation's ability to detect phishing sites targeting your users. This might not stop all phishing attacks, however it heightens the cost for the adversaries, meaning they have to come up with countermeasures to not get caught.
When it comes to the cost of the Logic App, it all depends on how many users your organisation have. A Logic App on a consumption plan are quite cost-effective, but you should monitor this to not get surprised.
One missing piece I still haven't figured out is a way to identify which user fell victim to the phish. With that information, we could add to the security automation by revoking sessions, perhaps disabling the account as well, improving remediation.
Let me know if you catch any phish 🎣 or if you have any questions. Again, thanks to Wesley Neelen for the idea!
Itj fårrå nålles, Haakon Baglo 😎